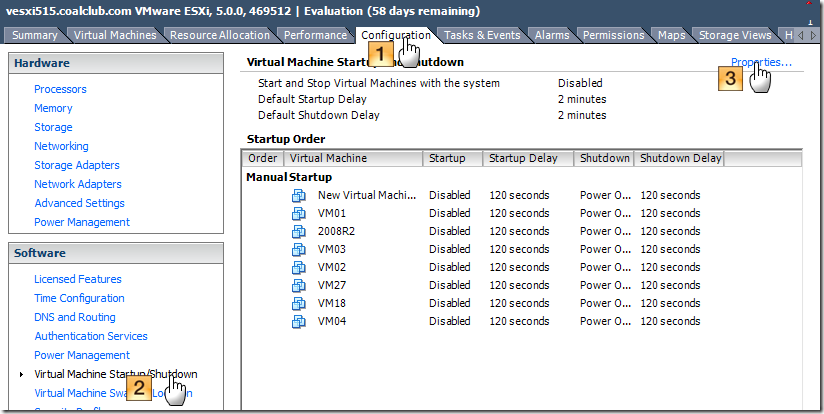
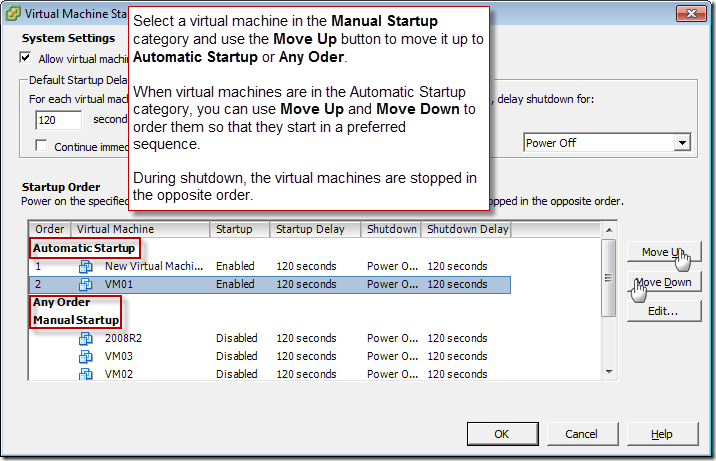
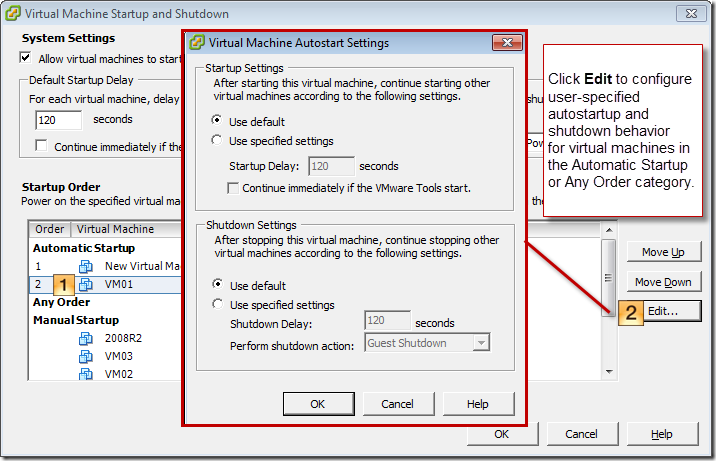
OpenVPN integration
with LDAP on Debian
OpenVPN, or Open Virtual Private Network, is a tool for creating
networking "tunnels" between and among groups of computers
that are not on the same local network. This is useful if you have
services on a local network and need to access them remotely but
don't want these services to be publicly accessible. By integrating
with OpenSSL, OpenVPN can encrypt all VPN traffic to provide a secure
connection between machines.
The OpenLDAP backend allows you to integrate all kinds of
applications and to realize centralized account management. This
tutorial shows you how to integrate OpenVPN into the OPenLDAP backend
on Debian 6.0; passwords will be stored in ldap and you can change
passwords through webmail.
This tutorial is based on Debian 6.0, so I suggest you set up a
minimal Debian 6.0 system with SSH; make sure you install all
updates. Install below packages.
1 Install OpenVPN
Install OpenVPN and ldap support:
apt-get install openvpn openvpn-auth-ldap
Install dnsmasq:
To forward DNS traffic through the VPN you will need to install
the dnsmasq package:
apt-get install dnsmasq
2 easy-rsa
The OpenVPN package provides a set of encryption-related tools
called "
easy-rsa". These scripts are located by
default in the
/usr/share/doc/openvpn/examples/easy-rsa/
directory. However, in order to function properly, these scripts
should be located in the
/etc/openvpn directory.
cp -R /usr/share/doc/openvpn/examples/easy-rsa/ /etc/openvpn
Configure Public Key Infrastructure Variables
Before we can generate the public key infrastructure for OpenVPN
we must configure a few variables that the easy-rsa scripts will use
to generate the scripts. These variables are set near the end of the
/etc/openvpn/easy-rsa/2.0/vars file. Here is an example of the
relevant values:
Edit
/etc/openvpn/easy-rsa/2.0/vars according to your
environment.
export KEY_COUNTRY="LK"
export KEY_PROVINCE="Western"
export KEY_CITY="Piliyandala"
export KEY_ORG="LK DOMAIN"
export KEY_EMAIL="sashika@suren.lk"
|
Initialize The Public Key Infrastructure (PKI)
Issue the following commands in sequence to internalize the
certificate authority and the public key infrastructure:
cd /etc/openvpn/easy-rsa/2.0/
chmod +rwx *
source ./vars
./clean-all
./pkitool --initca
Generate Certificates
With the certificate authority generated you can generate the
private key for the server. This script will also prompt you for
additional information. By default, the Common Name for this key will
be "server". You can change these values in cases where it
makes sense to use alternate values. To accomplish this, issue the
following command:
./pkitool --server server
Generate Diffie Hellman Parameters Link
The "Diffie Hellman Parameters" govern the method of key
exchange and authentication used by the OpenVPN server. Issue the
following command to generate these parameters:
./build-dh
Relocate Secure Keys
The keys and certificates for the server need to be relocated to
the
/etc/openvpn directory so the OpenVPN server process can
access them. These files are:
ca.crt
ca.key
dh1024.pem
server.crt
- server.key
cp keys/{ca.crt,ca.key,server.crt,server.key,dh1024.pem}
/etc/openvpn/
These files don't need to leave your server. Maintaining integrity
and control over these files is of the utmost importance to the
integrity of your server. If you ever need to move or back up these
keys, ensure that they're encrypted and secured.
3 Configure OpenVPN Support For LDAP Auth
Configure
OpenVPN auth OpenLDAP
Issue the following two commands in sequence to create the
/etc/openvpn/auth folder and copy the example files of OpenVPN auth
LDAP to the /etc/openvpn/auth directory.
mkdir /etc/openvpn/auth
cp
/usr/share/doc/openvpn-auth-ldap/examples/auth-ldap.conf
/etc/openvpn/auth
Now edit /etc/openvpn/auth/auth-ldap.conf:
auth-ldap.conf file
<LDAP>
# LDAP server URL
# Bind DN (If your LDAP server doesn't
support anonymous binds)
#
BindDN uid=Manager,ou=People,dc=example,dc=com
BindDN
uid=vpnuser,dc=example,dc=lk
# Bind Password
Password example.lk@123
# Network timeout (in seconds)
Timeout 15
# Enable Start TLS
#TLSEnable yes
# Follow LDAP Referrals (anonymously)
FollowReferrals yes
# TLS CA Certificate File
#TLSCACertFile /usr/local/etc/ssl/ca.pem
# TLS CA Certificate Directory
#TLSCACertDir /etc/ssl/certs
# Client Certificate and key
# If TLS client authentication is
required
#TLSCertFile /usr/local/etc/ssl/client-cert.pem
#TLSKeyFile /usr/local/etc/ssl/client-key.pem
# Cipher Suite
# The defaults are usually fine here
# TLSCipherSuite ALL:!ADH:@STRENGTH
</LDAP>
<Authorization>
# Base DN
#BaseDN "ou=People,dc=example,dc=com"
BaseDN "dc=example,dc=lk"
# User Search Filter
#SearchFilter "(&(uid=%u)(accountStatus=active))"
SearchFilter "(&(uid=%u))"
## This can be defined according to your LDAP server.
# Require Group Membership
RequireGroup false
# Add non-group members to a PF table
(disabled)
#PFTable ips_vpn_users
#<Group>
#BaseDN "ou=Groups,dc=example,dc=com"
#SearchFilter "(|(cn=developers)(cn=artists))"
#MemberAttribute uniqueMember
# Add group members to a PF table
(disabled)
#PFTable ips_vpn_eng
#</Group>
</Authorization>
4 Configuring OpenVPN
We'll now need to configure our server file. There is an example
file in the /usr/share/doc/openvpn/examples/sample-config-files
directory. Issue the following sequence of commands to retrieve the
example configuration files and move them to the required
directories:
cd /usr/share/doc/openvpn/examples/sample-config-files
gunzip
-d server.conf.gz
cp server.conf /etc/openvpn/
Now edit /etc/openvpn/server.conf:
server.conf file
Local 192.168.8.167 ## VPN server IP
address
port 1194
proto udp
dev tun
ca ca.crt
cert server.crt
key server.key # This file should be
kept secret
dh dh1024.pem
server 10.8.0.0 255.255.255.0
ifconfig-pool-persist ipp.txt
push "route 192.168.8.0
255.255.255.0"
##Your network
client-to-client
keepalive 10 120
comp-lzo
user nobody
group nogroup
persist-key
persist-tun
status openvpn-status.log
verb 3
###LDAP Integration
plugin
/usr/lib/openvpn/openvpn-auth-ldap.so
/etc/openvpn/auth/auth-ldap.conf
client-cert-not-required
Client Configuration
cp
/usr/share/doc/openvpn/examples/sample-config-files/client.conf
/etc/openvpn/easy-rsa/2.0/keys/client.ovpn
cd
/etc/openvpn/easy-rsa/2.0/keys
Edit the client.ovpn file to modify the following line:
Copy the client.ovpn and ca.crt files to your client system. Also
you can use mutt to send the files to your mailbox. You can log into
your email account and download the files.
apt-get install mutt zip
cd
/etc/openvpn/easy-rsa/2.0/keys
zip config.zip client.ovpn
ca.crt
mutt -s "OpenVPN client config files"
www@example.com -a /etc/openvpn/easy-rsa/2.0/keys/config.zip <
/usr/share/doc/openvpn/README
Client.ovpn
client
dev tun
proto udp
remote
192.168.8.167 1194
redirect-gateway
def1
resolv-retry
infinite
nobind
user nobody
group nogroup
persist-key
persist-tun
ca ca.crt
##
This is taken from VPN server
ns-cert-type
server
comp-lzo
verb 3
#LDAP authentication
auth-user-pass
If you are using
Ubuntu/Fedora Client Machine then you should issue below commad to
initialize VPN connectoin
openvpn client.ovpn
If you are using Windows Client
machine then you the follow below steps.
Installing OpenVPN GUI On Windows XP / Vista
Download the client software here:
http://openvpn.net/index.php/openvpn-client.html.
After installation,
put the client.ovpn and ca.crt files to
C:\Program Files\OpenVPN\config.
Now you can use the account www@example.com to connect to the vpn.

By deploying the above configuration, you will be able to forward
all traffic from client machines through your VPN and
encrypt it with transport layer security (TLS/SSL) between the
client machine and the VPN server.
Now you need to redirect traffic to Real network therfore you
should configure the VPN server as follows.
Now edit the
/etc/sysctl.conf file to
uncomment or add the following line to ensure that your system
is able to forward IPv4 traffic:
File excerpt:/etc/sysctl.conf
net.ipv4.ip_forward=1
Issue the following command to set this variable for the current
session:
echo 1 > /proc/sys/net/ipv4/ip_forward
Issue the following commands to configure iptables
to properly forward traffic through the VPN:
/sbin/iptables -A INPUT -p tcp -i eth0 --dport 1194 -j ACCEPT
/sbin/iptables -A FORWARD -i tun0 -j ACCEPT
/sbin/iptables -A INPUT -i tun0 -j ACCEPT
/sbin/iptables -A POSTROUTING --table nat -s 10.8.0.0/24 -o eth0 -j MASQUERADE
/sbin/iptables -A OUTPUT -j ACCEPT
Below is not required. With the above configuration you can
have fully running OpenVPN server.
This will enable all client traffic
except DNS queries to
be forwarded through the VPN. To forward DNS traffic through the VPN
you will need to install the
dnsmasq package
and modify the
/etc/opnevpn/server.conf
package. Begin by issuing the following command:
apt-get install dnsmasq
After completing the installation the configuration will need to be
modified so that dnsmasq is not listening on a public interface. You
will need to find the following lines in the configuration file and
make sure the lines are uncommented and have the appropriate values:
File excerpt:/etc/dnsmasq.conf
listen-address=127.0.0.1,10.8.0.1
bind-interfaces
This will configure dnsmasq to listen on localhost and the gateway IP
address of your OpenVPN's tun device.
When your system boots, dnsmasq will try to start prior to the
OpenVPN tun device being enabled. This will cause dnsmasq to fail at
boot. To ensure that dnsmasq is properly started at boot, you'll need
to modify your
/etc/rc.local file once
again. By adding the following line, dnsmasq will start after all the
init scripts have finished. You should place the restart command
below your iptables rules:
File excerpt:/etc/rc.local
/etc/init.d/dnsmasq restart
exit 0
Add the following directive to the
/etc/openvpn/server.conf
file:
File excerpt:/etc/openvpn/server.conf
push "dhcp-option DNS 10.8.0.1"
Finally, before attempting to connect to the VPN in any
configuration, restart the OpenVPN server and dnsmasq by issuing the
following commands:
/etc/init.d/openvpn restart
/etc/init.d/dnsmasq restart